Connected. Protected.
Thirdwayv helps your enterprise realize the full potential of loT connectivity. All while neutralizing security threats that can ruin the customer experience — and your reputation.
Why Thirdwayv?
Because when lives are on the line, we deliver.
Thirdwayv enables some of the world's most demanding and safety-critical loT services. Services where a patient's very well-being hinges upon our "getting it right". Time and again we've proven we can. And we bring those same assurances to other applications and markets that need secure and reliable operation.
Here is how we do it ![]()

![]()
End-to-end loT security, from the hardware up
We look at trusted IoT connectivity from an end-to-end, security-by-design perspective – and from the hardware up. In fact, our deep expertise at the semiconductor and component level is one of the things that sets us apart: unlike others, we can ensure trust from the core of the semiconductor chip and related components, to the cloud, across the entire solutions lifecycle.
You might even think of us as the "nucleus of trust" for your entire service or application. That's because we deliver the technologies that allow all the devices, connections, and applications to "trust" each other before any IoT transaction occurs. All to safeguard you – and your customers – against breaches, tampering, and fraud.

![]()
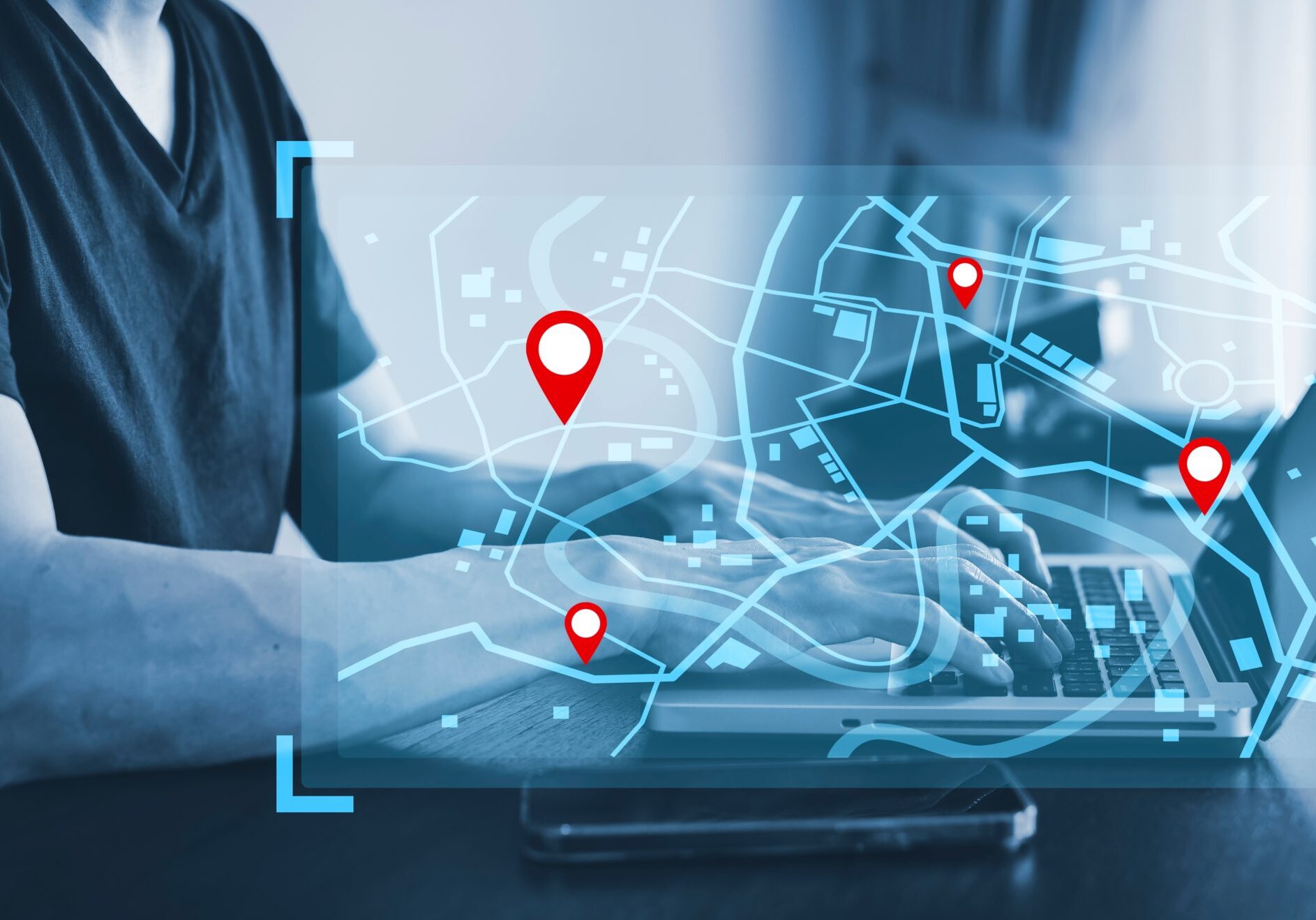
Connecting and securing millions of devices
We deploy applications ranging from consumer medical devices, to connected hospital and home healthcare, to asset tracking, to the connected car. That's a lot of territory covered, both in terms of geography and functionality. Proven. Trusted. Effective. These applications help enterprises like yours raise the bar on patient care and quality of life – and elevate the overall customer experience. Like we did for them, we can help you use IoT connectivity to deliver on your all brand promises. If not far exceed them.

![]()
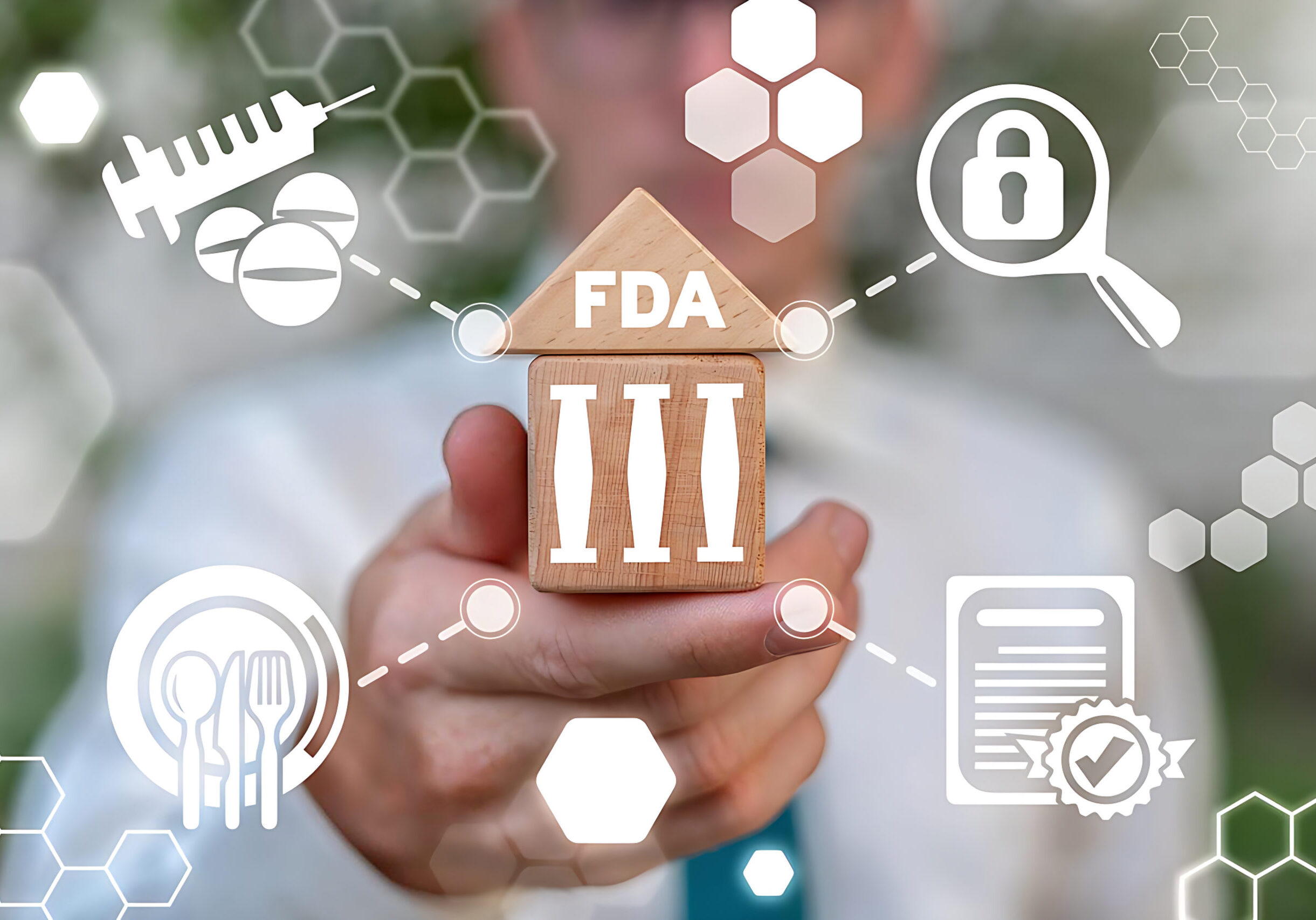
FDA clearances received... enabling partners to meet FDA guidelines
When you're on the forefront of technology, there are few standards and best practices already in place. But we're changing that. Our products enable partners to meet FDA cybersecurity guidelines - just by integrating with our Software Development Kits. That means we're creating new standards for applications and providing hardware roots of trust for connected medical devices, thus shortening the time it takes for you to bring those applications to market.

![]()
Easy deployments that close the gap between investment and revenue
Our software-as a service business model delivers the fastest path to loT application deployment. And that translates into the fastest returns on your technology investment.
Additionally, we can help you scale across multiple applications and quickly incorporate new capabilities. It's done by leveraging proven technology and security assurances that we've already implemented across the healthcare sector. Because if we can get it right in the most highly regulated and safety-critical environment, we can easily adapt what's in-place to yours.
Finally, as semiconductor experts, we can help as needed with cost-reducing hardware, rapid prototyping and even industrial design – all while keeping security and connectivity features at the highest levels.
Company
We're invested in technology. And also in you.
We've built our business on trust. Not only when it comes to loT connectivity and security, but also when it comes to relationships. Because who you can trust is as important as anything else. Perhaps even more so.
![]()
Our Mission is simple
We live in exciting times, filled with never-before-seen opportunity. But inextricably linked with the technological potential are threats that can be even greater in scope. Threats that can destroy the very thing that's central to any brand – its reputation.
Our mission at Thirdwayv is straightforward: we want to help take the anxiety out of the IoT.
We want to help your enterprise move safely beyond place-to-place and person-to-person communications to a new wave of thing-to-thing networks. A THIRDWAYV, if you will. One without worries. One where we've secured every element of the system and all of the devices connected to it. Our goal is an IoT you can trust, for safety-critical applications and services that depend on it.
![]()
Our Values are what ground us
Connection
Yes, we're in the business of peer-to-peer connectivity. But we believe we're enabling something far greater – meaningful human connection. That's because we believe in the power of the IoT to improve how the world monitors and manages disease. All while automating processes and creating better, more personalized user experiences. The result is an increased quality of life for millions. And a deeper connection between you and your customers.
Integrity
We believe 100% in the integrity of our solutions. That's because we believe 100% in the integrity of our people. We've assembled a team of hardware and software engineers who believe whole-heartedly in what they do. They're deep thinkers. They like to challenge convention. And they're experts in all aspects of IoT security, efficiency, and reliability. We settle for nothing less here. Because we know your enterprise can't afford to, either.
Collaboration
Our clients are the heroes of our story. They're equal parts dreamers and doers, all invested in exceeding the brand promises they make to customers. They challenge us every day. And we help them further push the envelope. We're grateful to partner with some of the world's leading brands. Together, we pioneer ground-breaking solutions that change lives and power a better, brighter, smarter world. It's our privilege to collaborate with each of them.
Use Cases
We're tested and trusted by global brands. Now, what can we do for you?
Thirdwayv delivers important new loT capabilities across all broadly-adopted wireless protocols. They're deployed by industry-leading customers in some of the highest-value applications — from medical devices to track and trace solutions for surgical implants. When you require the utmost in safety and reliability, Thirdwayv leads the charge.
Healthcare & Consumer Medical Devices
Your patients lives are on the line. And so is your reputation. We'll help you improve the quality of their future, while safeguarding yours.
Connected Home Healthcare
We’re making at-home care a reality and helping patients raise their quality of life…
Read MoreConnected Hospitals
We’re helping hospitals track and manage everything from critical assets to people and more…
Read MoreElectrical/Neuro Stimulation and Drug Delivery
From pacemakers, nerve stimulators, defibrillators, to insulin pumps, we’re enabling secure solutions for electrical stimulation and automated drug delivery…
Read MoreBiometric Monitoring
From thermometers, blood pressure monitors, glucose meters and pulse oximeters to heart rate monitors, we’re helping to change the landscape of disease management with real-time, connected monitoring…
Read MoreSecure Over-the-Air (OTA) ECU Firmware Upgrades
We make it easy to use the industry standard in vehicle software updates…
Read MoreAutosar Security Components
We’re filling the gap between what Autosar provides and what you’re left to figure out on your own…
Read MoreInfotainment System Security
We created a secure, lightweight add-on that forms a protective shield around Android Auto…
Read MoreAutomobile Access and Control — Smartphone Keyless Entry
We have the end-to-end solution that secures communication and thwarts hackers…
Read MoreRetail Item Tracking
Track-and-trace solutions used in the industrial and logistics setting can also be employed for securing and improving efficiencies in the retail supply chain. These real-time asset-tracking solutions improve inventory-management visibility as products move from the shipper, to the receiving dock, to the retail shelf and ultimately to the cash register in the hands of a customer…
Read MoreIndoor Asset Location Tracking
Healthcare organizations often must track the precise location of life-critical assets and controlled substances inside their facilities, in real time. These might be a “crash carts” used to rapidly transport and dispense life-critical emergency medications and equipment…
Read MoreConsigned Inventory Management
Many hospital assets are sold and managed on the hospital premises by their suppliers, who only issue invoices for them when they are used. Both the supplier and the hospital need maximum visibility to this consigned inventory…
Read More360-degree Track and Trace
You need end-to-end control and verification across the product journey. And we’re making that simpler, more affordable, and more secure than ever. Ours is the first affordable solution with applications in pharmaceutical manufacturing, food safety, and industrial control…
Read MoreProducts
Comprehensive. Scalable. Backed by FDA-cleared, patent-protected technology.
Introducing AppAuth™ and SecureConnectivity™, the first software solutions in a suite of products that meet the approvals of FDA cyber security stacks. Now you can eliminate vulnerabilities in communication between the Phone and Thing, as well as the Phone and Cloud.
When Communication becomes compromised, so does your brand
You assume apps and communication transport mechanisms like Bluetooth, NFC, LTE, Ethernet, and others are secure. But are they? While their basic security mechanisms mitigate some breaches, other threats – like holes in one-size-fits-all authentication and eavesdropping – are far less contained. Here’s how to lock down both app and channel, and uphold the safety promises you make.
Product Overview
4 Key Products enabling Trust, Security & Interoperability Solutions
SeamlessConnect™
Connect “Things” to the Internet in a seamless and transparent fashion. Authorized devices connect automatically to intermediate hardware gateways or Smartphone Apps within communication range.

AppAuth™
Authenticate customers and their devices, protect your app from malware attacks, and validate system commands and components via remote attestation. You’ll ensure that all system elements can be trusted at all times.

SecureConnectivity™
Protects the privacy and integrity of customer’s information by creating a secure tunnel at the application layer. This secure tunnel protects data without relying on the underlying security, or lack thereof, of the transport mechanism being used.
(i.e. Bluetooth, NFC, LTE, Ethernet, etc.)

RecordAuth™
Using Blockchain technology, RecordAuth™ ensures the authenticity of data entered into the system by various sensors or entities within a supply chain or financial ecosystem.

SeamlessConnect™
Connect “Things” to the Internet in a seamless and transparent fashion. Authorized devices connect automatically to intermediate hardware gateways or Smartphone Apps within communication range.
AppAuth™
Authenticate customers and their devices, protect your app from malware attacks, and validate system commands and components via remote attestation. You’ll ensure that all system elements can be trusted at all times.

Product Overview
4 Key Products enabling Trust, Security & Interoperability Solutions

SecureConnectivity™
Protects the privacy and integrity of customer’s information by creating a secure tunnel at the application layer. This secure tunnel protects data without relying on the underlying security, or lack thereof, of the transport mechanism being used.
(i.e. Bluetooth, NFC, LTE, Ethernet, etc.)
RecordAuth™
Using Blockchain technology, RecordAuth™ ensures the authenticity of data entered into the system by various sensors or entities within a supply chain or financial ecosystem.

Security
We take you from "vulnerable" to "impenetrable".
Thirdwayv solves the IoT security challenge at every point of vulnerability. We start by establishing our "nucleus of trust" with the factory hardware security module (HSM). Then we ensure trusted provisioning, plus secure communications and networking across all devices – including nodes, endpoints, apps, gateways, and even the cloud infrastructure.
If we can safeguard a surgical implant, we can safeguard anything
Imagine a device that performs a "mission critical" function. On the one hand, it's durable and complex. On the other, it's a delicate assemblage of form, function, connectivity, and security. Perhaps none more important than the latter.
Our cybersecurity software stack for IoT applications provides immunity against a variety of attacks. It's the definitive answer to securing safety-critical applications – from surgical implants, to drug delivery pumps and beyond.
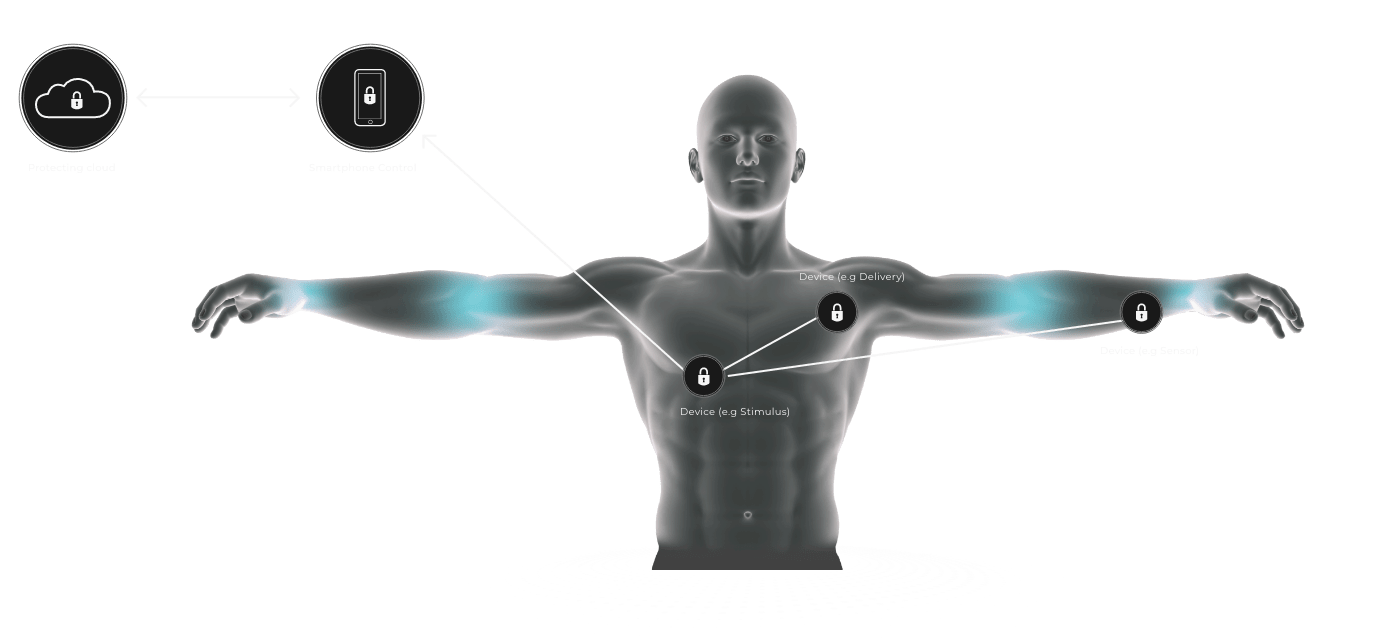
We include all necessary components for communications and control between smartphones and the cloud, and to and from IoT devices. Other key elements include.
Smartphone operating system security that extends across the app and platform.
IoT device security and key management.
Over-the-air upgrades for IoT devices.
The key elements of IoT protection – and how we address them
Newsroom/Blog
We take you from "vulnerable" to "impenetrable".
ThirdWayv solves the IoT security challenge at every point of vulnerability. We start by establishing our "nucleus of trust" with the factory hardware security module (HSM). Then we ensure trusted provisioning, plus secure communications and networking across all devices – including nodes, endpoints, apps, gateways, and even the cloud infrastructure.
Thirdwayv and Medcrypt Forge Partnership to Advance Medical Device Cybersecurity and Interoperability
Irvine, CA & San Diego, CA – October 28, 2025 –Thirdwayv Inc., a leader in secure software solutions for connected medical devices, and Medcrypt Inc., a premier provider of medical device cybersecurity and vulnerability management solutions, announced today the signing of an agreement to jointly advance cybersecurity and interoperability standards and solutions across the connected…
know moreProtecting connected RPM solutions
Many legislative and regulatory mandates or guidelines are now moving the industry toward an internet of medical things that builds on proven, multi-layered security strategies. These strategies have already proven successful in applications like diabetes management and medication adherence and can be extended to pacemakers, cardiac monitors and many other safety-critical connected remote patient monitoring…
know moreCuring MedTech’s Cybersecurity Contagion
There is growing and coordinated momentum behind the goal of ensuring connected medical devices improve people’s lives without introducing them to cybersecurity threats and associated safety risks. There also is a proven playbook for implementing the type of multi-layered, security-by-design strategies these initiatives advocate.
know moreMedtech cybersecurity compliance
Passage of the Omnibus bill has given the FDA statutory authority to create a world where no one who benefits from connected medical technologies must worry about hackers trying to exploit these technologies. The latest draft FDA guidance takes another big step toward aligning medical device requirements with the industry’s proven cybersecurity best practices. Equally…
know morePopularity of Remote Patient Monitoring Skyrockets — Is it Secure?
A recent report from commercial intelligence platform provider Definitive Healthcare revealed that remote patient monitoring insurance reimbursement claims rose 1,294% from January 2019 to November 2022. It’s likely that a desire to minimize contact during the pandemic drove much of this demand. But remote patient monitoring claims continued to grow even after people resumed face-to-face…
know moreSecuring real-time location system solutions
Real-time location system (RTLS) solutions got their start in government and the military during the 1990s, and have since been adopted in manufacturing, logistics and aerospace, among other applications. More recently they are seeing growing use in healthcare consignment inventory management and retail item tracking. In both applications, RTLS must be implemented with a security-by-design…
know moreCountdown to Safer Medical Devices
A six-month clock started ticking late last year, counting down to the FDA’s new deadline for updating its public-facing guidance for improving the cybersecurity of medical devices. This requirement became law on Dec. 29, 2022, as part of a $1.7 trillion Omnibus Appropriations Bill that also includes new rules for submitting applicable medical devices to…
know moreGetting Real about Real-Time Location Systems
Real-Time Location Systems, or RTLS, emerged in the 1990s for use by government and military entities. The technology has been adopted in manufacturing, logistics and aerospace applications for years. Now it is coming into its own in a growing variety of other applications, from healthcare consignment inventory management to retail item tracking. It’s time to…
know moreImprove Operational Efficiency And Combat Fraud With Secure Real-Time Location Systems
Today’s IoT-based RTLS systems can ensure that high-value consumer products are accurately accounted for to the retail point of sale. To be successful, however, the solutions must be protected from cyber threats at each step of the journey using a multi-layered, “security-by-design” strategy that ensures continuous availability of critical inventory status for all items and…
know moreThirdwayv to Showcase Solutions for Connecting and Protecting Asset Management, Healthcare and Other Applications at IoT World
Company will also participate in panel session on improving visibility in the supply chain through asset tracking Irvine, Calif., Oct. 25, 2022 – Thirdwayv, a leading provider of end-to-end connectivity and security solutions for IoT applications, today announced it will be exhibiting at IoT World to show applications ranging from consignment inventory and other asset-management…
know moreLet's Talk
The future of your enterprise is only a few keystrokes away
Ready to start a conversation? We are too. Simply complete the fields below and let's start talking about the shape of what's to come. We'll help you take full advantage of what's happening in our industry. All while guiding and safeguarding your enterprise every step of the way.