![]()
Our Values are what ground us
Healthcare & Consumer Medical Devices
Your patients lives are on the line. And so is your reputation. We'll help you improve the quality of their future, while safeguarding yours.
Sorry, we couldn't find any posts. Please try a different search.
Sorry, we couldn't find any posts. Please try a different search.
Sorry, we couldn't find any posts. Please try a different search.
Products
Comprehensive. Scalable. Backed by FDA-cleared, patent-protected technology.
Introducing AppAuth™ and SecureConnectivity™, the first software solutions in a suite of products that meet the approvals of FDA cyber security stacks. Now you can eliminate vulnerabilities in communication between the Phone and Thing, as well as the Phone and Cloud.
When Communication becomes compromised, so does your brand
You assume apps and communication transport mechanisms like Bluetooth, NFC, LTE, Ethernet, and others are secure. But are they? While their basic security mechanisms mitigate some breaches, other threats – like holes in one-size-fits-all authentication and eavesdropping – are far less contained. Here’s how to lock down both app and channel, and uphold the safety promises you make.
Product Overview
4 Key Products enabling Trust, Security & Interoperability Solutions
SeamlessConnect™
Connect “Things” to the Internet in a seamless and transparent fashion. Authorized devices connect automatically to intermediate hardware gateways or Smartphone Apps within communication range.

AppAuth™
Authenticate customers and their devices, protect your app from malware attacks, and validate system commands and components via remote attestation. You’ll ensure that all system elements can be trusted at all times.

SecureConnectivity™
Protects the privacy and integrity of customer’s information by creating a secure tunnel at the application layer. This secure tunnel protects data without relying on the underlying security, or lack thereof, of the transport mechanism being used.
(i.e. Bluetooth, NFC, LTE, Ethernet, etc.)

RecordAuth™
Using Blockchain technology, RecordAuth™ ensures the authenticity of data entered into the system by various sensors or entities within a supply chain or financial ecosystem.

SeamlessConnect™
Connect “Things” to the Internet in a seamless and transparent fashion. Authorized devices connect automatically to intermediate hardware gateways or Smartphone Apps within communication range.
AppAuth™
Authenticate customers and their devices, protect your app from malware attacks, and validate system commands and components via remote attestation. You’ll ensure that all system elements can be trusted at all times.

Product Overview
4 Key Products enabling Trust, Security & Interoperability Solutions

SecureConnectivity™
Protects the privacy and integrity of customer’s information by creating a secure tunnel at the application layer. This secure tunnel protects data without relying on the underlying security, or lack thereof, of the transport mechanism being used.
(i.e. Bluetooth, NFC, LTE, Ethernet, etc.)
RecordAuth™
Using Blockchain technology, RecordAuth™ ensures the authenticity of data entered into the system by various sensors or entities within a supply chain or financial ecosystem.

Security
We take you from "vulnerable" to "impenetrable".
Thirdwayv solves the IoT security challenge at every point of vulnerability. We start by establishing our "nucleus of trust" with the factory hardware security module (HSM). Then we ensure trusted provisioning, plus secure communications and networking across all devices – including nodes, endpoints, apps, gateways, and even the cloud infrastructure.
If we can safeguard a surgical implant, we can safeguard anything
Imagine a device that performs a "mission critical" function. On the one hand, it's durable and complex. On the other, it's a delicate assemblage of form, function, connectivity, and security. Perhaps none more important than the latter.
Our cybersecurity software stack for IoT applications provides immunity against a variety of attacks. It's the definitive answer to securing safety-critical applications – from surgical implants, to drug delivery pumps and beyond.
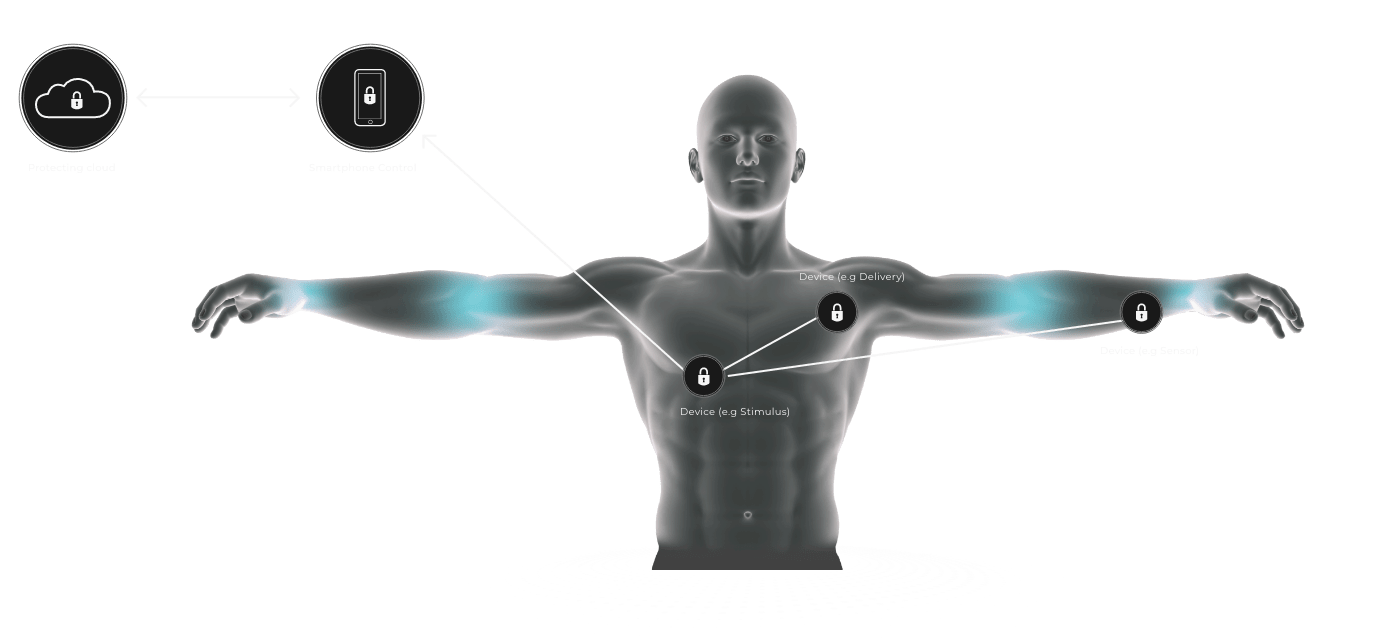
We include all necessary components for communications and control between smartphones and the cloud, and to and from IoT devices. Other key elements include.
Smartphone operating system security that extends across the app and platform.
IoT device security and key management.
Over-the-air upgrades for IoT devices.
The key elements of IoT protection – and how we address them
Newsroom/Blog
We take you from "vulnerable" to "impenetrable".
ThirdWayv solves the IoT security challenge at every point of vulnerability. We start by establishing our "nucleus of trust" with the factory hardware security module (HSM). Then we ensure trusted provisioning, plus secure communications and networking across all devices – including nodes, endpoints, apps, gateways, and even the cloud infrastructure.
Protecting connected RPM solutions
Many legislative and regulatory mandates or guidelines are now moving the industry toward an internet of medical things that builds on proven, multi-layered security strategies. These strategies have already proven successful in applications like diabetes management and medication adherence and can be extended to pacemakers, cardiac monitors and many other safety-critical connected remote patient monitoring…
know moreCuring MedTech’s Cybersecurity Contagion
There is growing and coordinated momentum behind the goal of ensuring connected medical devices improve people’s lives without introducing them to cybersecurity threats and associated safety risks. There also is a proven playbook for implementing the type of multi-layered, security-by-design strategies these initiatives advocate.
know moreMedtech cybersecurity compliance
Passage of the Omnibus bill has given the FDA statutory authority to create a world where no one who benefits from connected medical technologies must worry about hackers trying to exploit these technologies. The latest draft FDA guidance takes another big step toward aligning medical device requirements with the industry’s proven cybersecurity best practices. Equally…
know morePopularity of Remote Patient Monitoring Skyrockets — Is it Secure?
A recent report from commercial intelligence platform provider Definitive Healthcare revealed that remote patient monitoring insurance reimbursement claims rose 1,294% from January 2019 to November 2022. It’s likely that a desire to minimize contact during the pandemic drove much of this demand. But remote patient monitoring claims continued to grow even after people resumed face-to-face…
know moreSecuring real-time location system solutions
Real-time location system (RTLS) solutions got their start in government and the military during the 1990s, and have since been adopted in manufacturing, logistics and aerospace, among other applications. More recently they are seeing growing use in healthcare consignment inventory management and retail item tracking. In both applications, RTLS must be implemented with a security-by-design…
know moreCountdown to Safer Medical Devices
A six-month clock started ticking late last year, counting down to the FDA’s new deadline for updating its public-facing guidance for improving the cybersecurity of medical devices. This requirement became law on Dec. 29, 2022, as part of a $1.7 trillion Omnibus Appropriations Bill that also includes new rules for submitting applicable medical devices to…
know moreGetting Real about Real-Time Location Systems
Real-Time Location Systems, or RTLS, emerged in the 1990s for use by government and military entities. The technology has been adopted in manufacturing, logistics and aerospace applications for years. Now it is coming into its own in a growing variety of other applications, from healthcare consignment inventory management to retail item tracking. It’s time to…
know moreImprove Operational Efficiency And Combat Fraud With Secure Real-Time Location Systems
Today’s IoT-based RTLS systems can ensure that high-value consumer products are accurately accounted for to the retail point of sale. To be successful, however, the solutions must be protected from cyber threats at each step of the journey using a multi-layered, “security-by-design” strategy that ensures continuous availability of critical inventory status for all items and…
know moreThirdwayv to Showcase Solutions for Connecting and Protecting Asset Management, Healthcare and Other Applications at IoT World
Company will also participate in panel session on improving visibility in the supply chain through asset tracking Irvine, Calif., Oct. 25, 2022 – Thirdwayv, a leading provider of end-to-end connectivity and security solutions for IoT applications, today announced it will be exhibiting at IoT World to show applications ranging from consignment inventory and other asset-management…
know moreThirdwayv to Participate in First Industry Event Focused on New IEEE Standard for Connecting and Protecting Digital Diabetes Devices
Company Advisory Board Members Will Join Other Experts at the Event to Discuss How the Industry is Now “Securing the IoT Ecosystem for Medical Devices” Irvine, Calif., Sept. 12, 2022 – Thirdwayv, a leading provider of end-to-end connectivity and security solutions for IoT applications, today announced it will participate in the first event to celebrate…
know moreLet's Talk
The future of your enterprise is only a few keystrokes away
Ready to start a conversation? We are too. Simply complete the fields below and let's start talking about the shape of what's to come. We'll help you take full advantage of what's happening in our industry. All while guiding and safeguarding your enterprise every step of the way.